NodeJS - Auth Bypass
Running the app on Docker
$ sudo docker pull blabla1337/owasp-skf-lab:js-auth-bypass$ sudo docker run -ti -p 127.0.0.1:5000:5000 blabla1337/owasp-skf-lab:js-auth-bypassReconnaissance
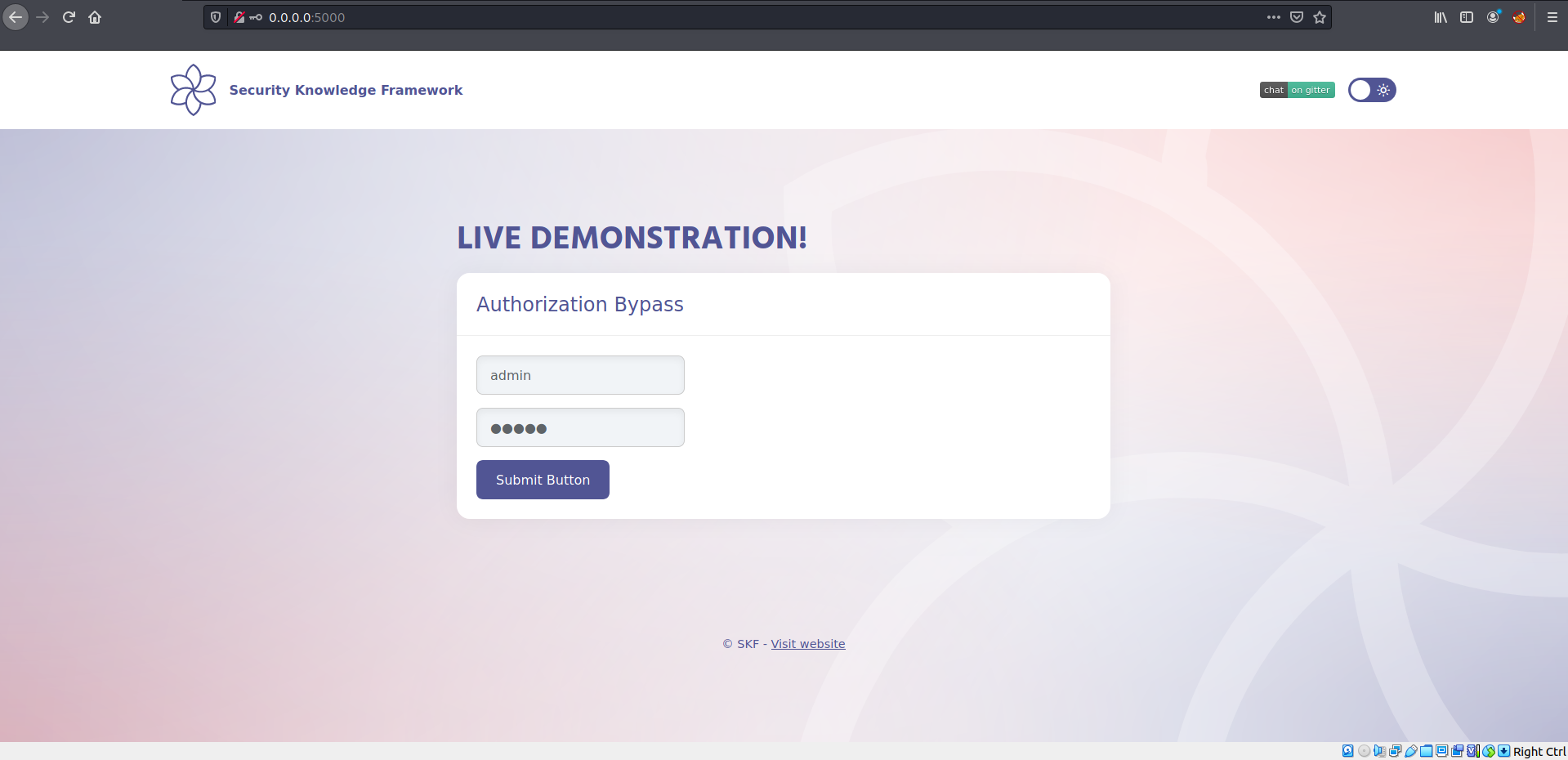
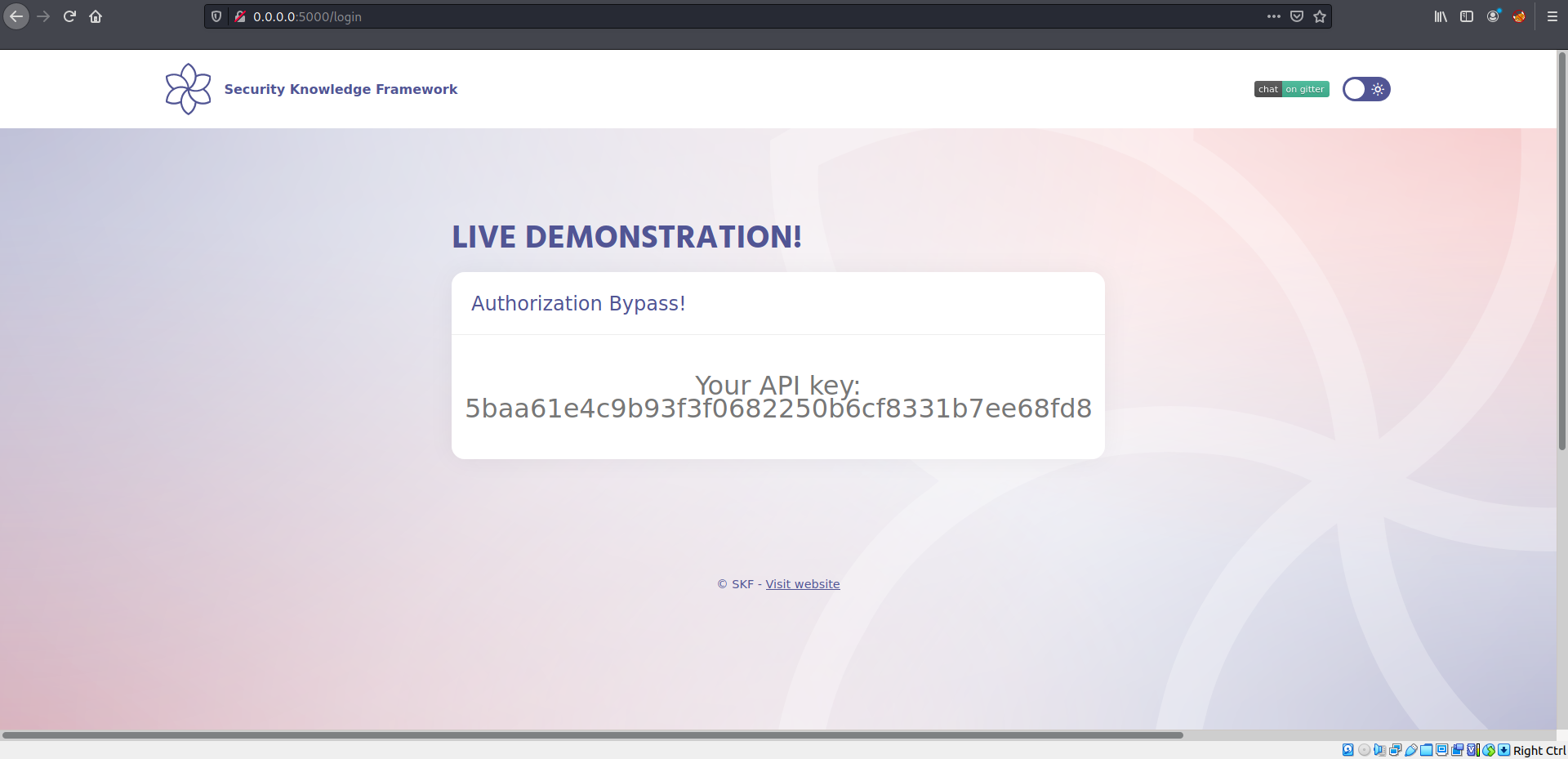
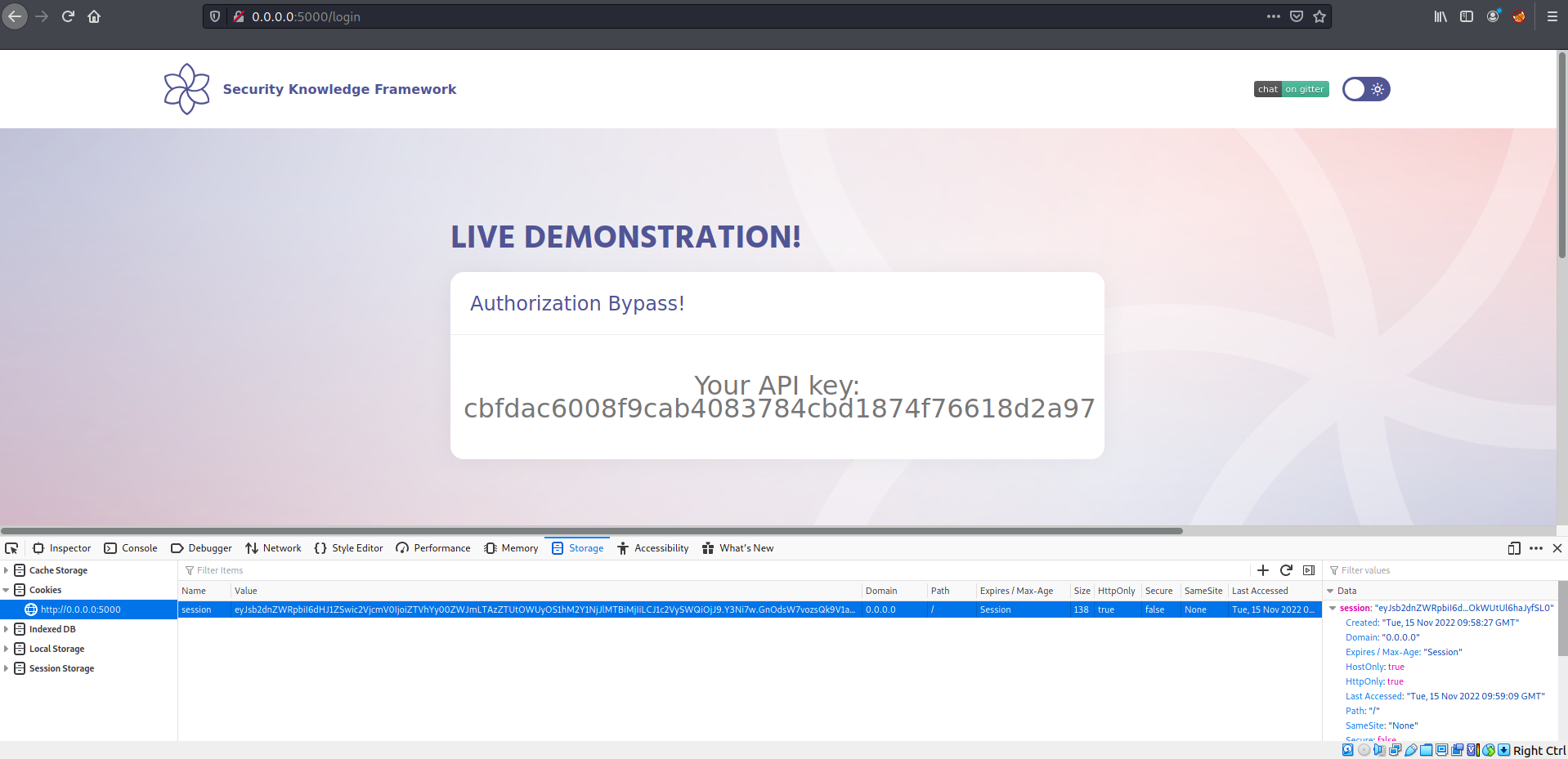
Exploitation
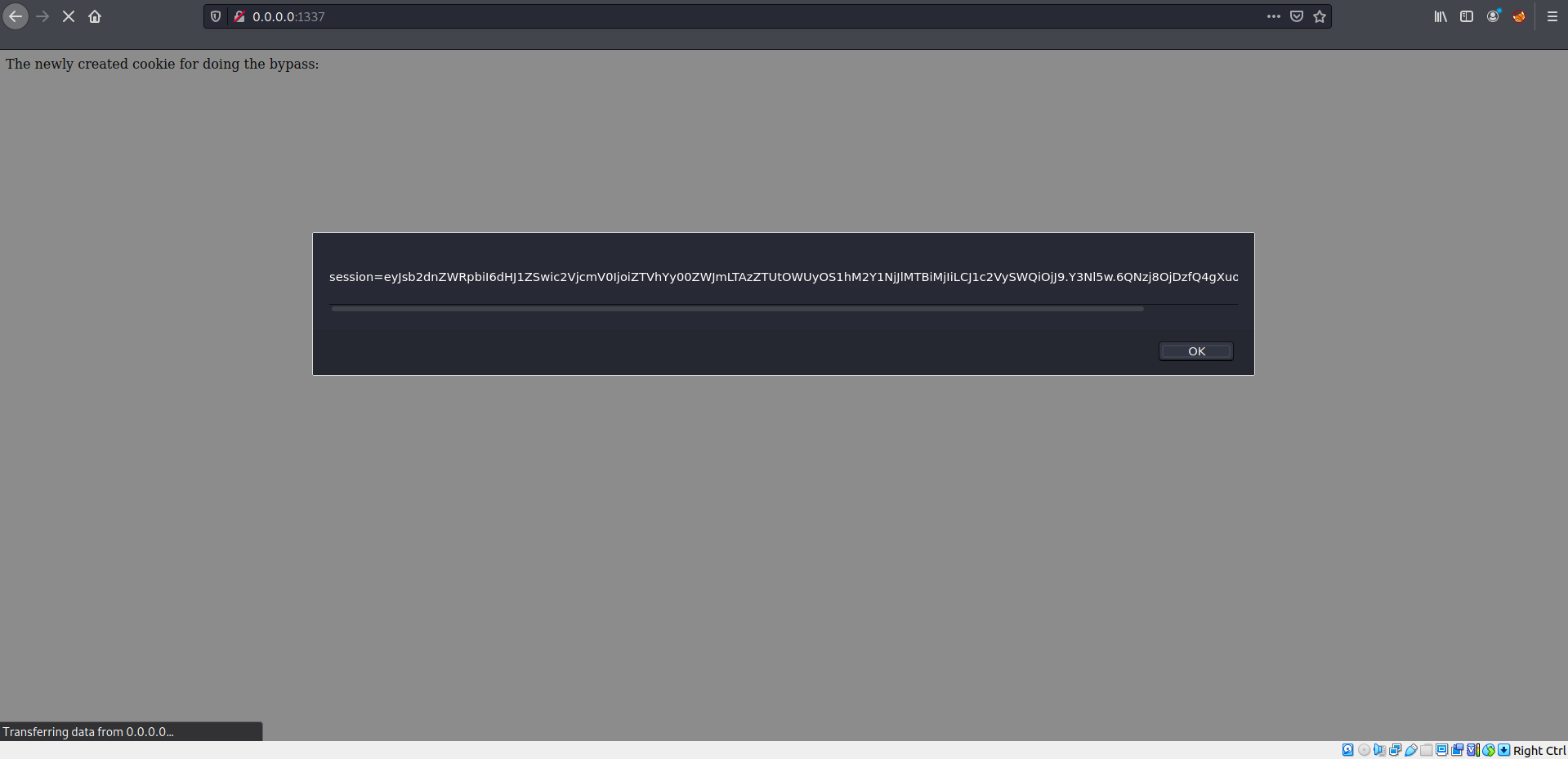
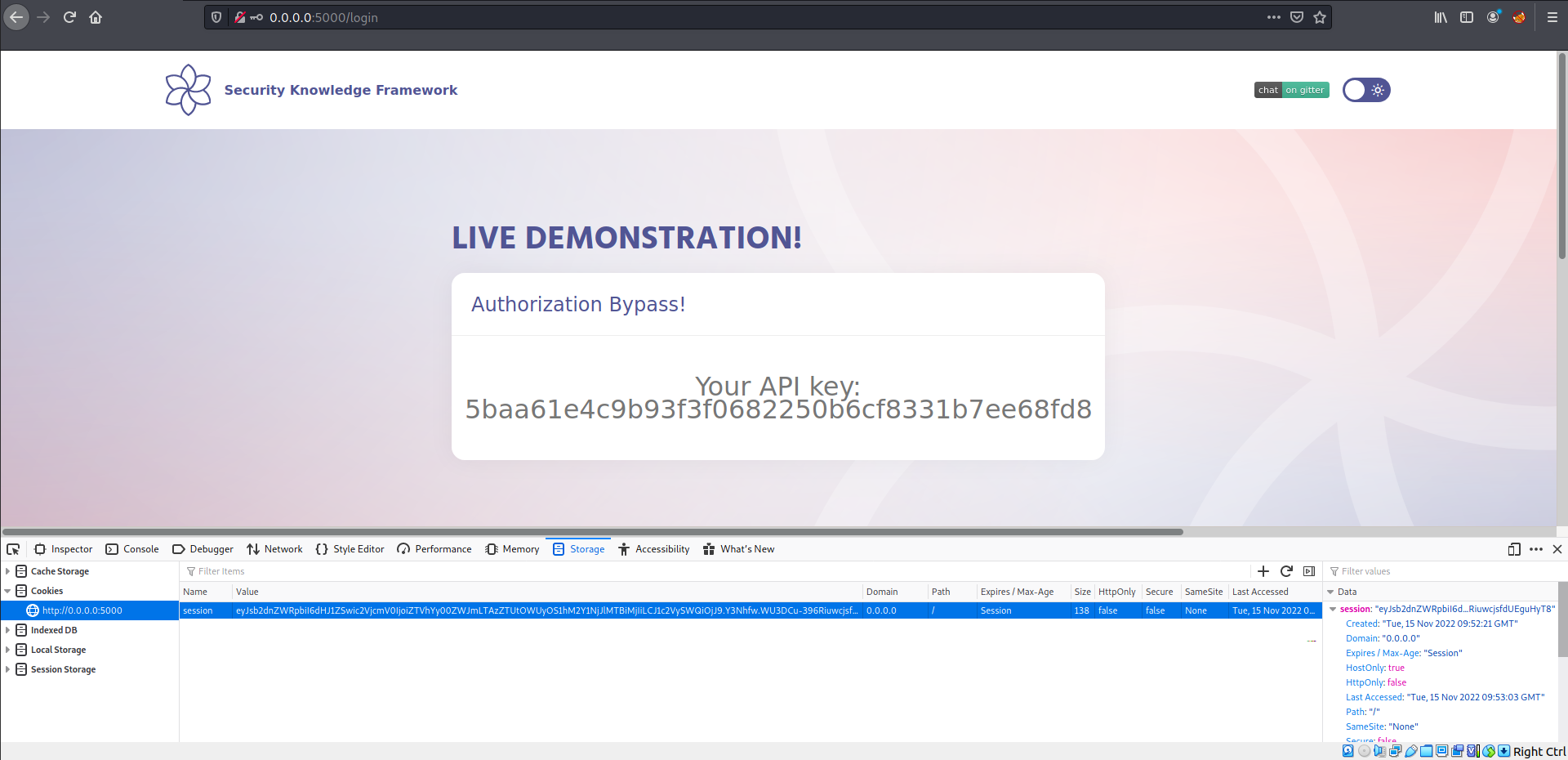
Additional sources
Last updated
Was this helpful?